 A talk given by Joost van Dijk from Yubico at the 2023 Platform Summit in Stockholm.
A talk given by Joost van Dijk from Yubico at the 2023 Platform Summit in Stockholm.
Today’s web APIs often require some form of API access management and identity control for their users, and these are usually implemented using protocols like OAuth and OpenID Connect.
Not surprisingly, there are many efforts towards improving the security of OAuth flows, such as replacing bearer-tokens with stronger alternatives (such as with DPoP) or other high-security OAuth extensions (like FAPI, PAR, JAR, JARM, etc.) However, while being fundamental to API security whenever a user is involved, the method by which user authentication is performed is declared out of scope in the OAuth/OIDC specifications.
For this reason we need to separately consider improving the security of the user authentication process itself. Traditionally, this has been done using some form of Multi-Factor Authentication (MFA).
Attacks targeting end-users such as phishing are a huge problem today, but many MFA methods are either not phishing-resistant or have serious usability issues and are therefore only seen within some high-assurance enterprises scenarios.
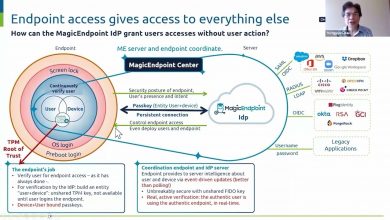
Passkeys are phishing-resistant by design, can replace both PKI tokens as seen in enterprises and weak consumer MFA methods while also improving usability with a familiar user interface.
They can serve both enterprise scenarios using security keys, or consumer scenarios using platform authenticators built-in to mobile and desktop devices.
The underlying FIDO2 open standards are supported today by all major browser and platform vendors. Now is the time for identity and platform providers to start securing user authentication for their services using passkeys.
In this presentation, we’ll dive into what passkeys are, the issues they solve, and how they can replace passwords and less secure forms of MFA like one-time passwords.



037311
I was reading some of your content on this website and I believe this web site is
rattling informative! Keep on putting up.Blog monry